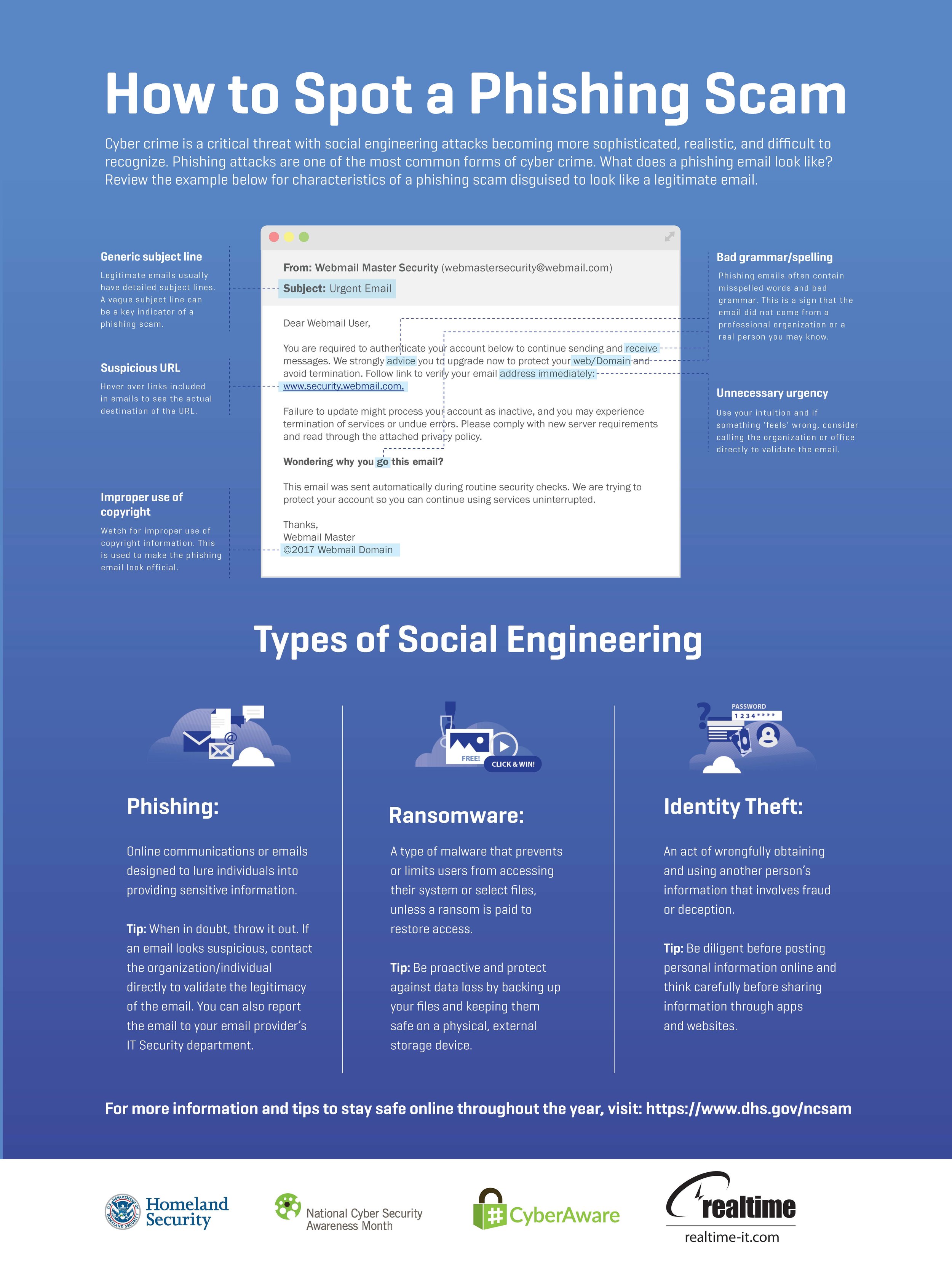
How to Spot a Phishing Scam
Millions of people are targets of phishing scams each day. Cyber criminals use a variety of tricks to disguise themselves as legitimate companies, your colleagues, and people you would normally trust. Make sure you know who you are really communicating with and be careful of suspicious links.
October is National Cyber Security Awareness Month.
DOES SOMETHING SEEM "PHISHY" TO YOU?
Millions of people are targets of phishing scams each day. Cyber criminals use a variety of tricks to disguise themselves as legitimate companies, your colleagues, and people you would normally trust. Make sure you know who you are really communicating with and be careful of suspicious links.
RealTime team creates Ransomware awareness
This isn't our normal blog post, but this short 'Live' Facebook video gives heart and humor to the serious subject of Ransomware.
RealTime educating the general public on Ransomware during the 2017 Foster Fest in downtown Dothan, AL.
This isn't our normal blog post, but this short 'Live' Facebook video gives heart and humor to the serious subject of Ransomware. Watch this brief video showing some of our RealTime team in action. If you have a question about how Ransomware can affect your business, email us at info@realtime-it.com or call (334) 678-1417.
*Also, don't forget to follow us on Facebook! Look at what you're missing...
The Equifax Breach and You
We’ve all probably heard of the recent, highly publicized Equifax breach and cyber extortion. In light of this are other breaches, you have probably also formed the impression that, if you are an adult in the U.S., your basic personal information is probably for sale somewhere. Unfortunately, you’re right. There is no airtight solution, but there are some things you can do.
Equifax setup a website, https://www.equifaxsecurity2017.com/ So that you can check if your personal information was included in this latest breach. This page has a link to https://TrustedIDPremier.com which can check if your data saw part of the breach. You can sign up for their ID protection service from there if you’d like.
We’ve all probably heard of the recent, highly publicized Equifax breach and cyber extortion. In light of this are other breaches, you have probably also formed the impression that, if you are an adult in the U.S., your basic personal information is probably for sale somewhere. Unfortunately, you’re right. There is no airtight solution, but there are some things you can do.
1. There are three main credit reporting agencies (CRAs) in the U.S.: Equifax, Experian, and TransUnion. Innovis is also growing in size. The information about you in a credit report from any one of these CRAs is almost the same. You are entitled to one free credit report from each of the three main CRAs per year. Consider obtaining one report from each CRA once every four months. You can do that here: https://www.annualcreditreport.com/. Check it carefully for errors and accounts that aren’t yours.
2. Next, consider placing a credit freeze on your identity. You will also see this referenced as a security freeze. With a freeze in place, lenders need to obtain your permission before they can get a copy of your credit report, making it hard for identity thieves to open new accounts with your information. A credit freeze does not reduce your credit score, but will require you to lift the freeze when obtaining a mortgage, purchasing insurance, applying for a job, etc. You can learn more about the credit freeze process here: https://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs#what. Another good discussion is available here: http://consumersunion.org/research/consumers-unions-guide-to-security-freeze-protection/.
a. Freeze quick links
i. Equifax – 800-349-9960, https://freeze.equifax.com
ii. Experian – 888-397-3742, https://experian.com/freeze
iii. TransUnion – 888-909-8872, https://transunion.com/freeze
3. You can also place a fraud alert on your identity. It’s not as effective as a credit freeze, but does obligate a business to verify your identity before credit can be issued, although this process is far from perfect. More information on the types of fraud alerts and the process to put an alert in place is available here: https://www.consumer.ftc.gov/articles/0275-place-fraud-alert
4. Opt out of pre-approved credit offers that can be taken from the mail stream and used for fraud. Begin the process at www.optoutprescreen.com.
The question of whether or not to subscribe to a credit monitoring service, even a free one like Equifax is offering (for a year), comes down to personal choice. Despite the marketing hype, none of these services prevent identity theft. At best, credit monitoring services alert you after your identity is stolen. The steps above make it less likely that you will fall victim in the first place.
If you suspect you have been the victim of identity theft, a good response roadmap is available at https://identitytheft.gov/.
Hurricane Preparedness Checklist
As Hurricane Irma makes its way towards Florida and the Southeast U.S., now is the time to take action and be prepared to protect your computers, printers, files and data.
As Hurricane Irma makes its way towards Florida and the Southeast U.S., now is the time to take action and be prepared to protect your computers, printers, files and data.
1. ENSURE YOU HAVE A BACKUP
- Don't wait until the day before a hurricane to backup your files! It's good practice to frequently backup your data files. We recommend a hybrid-cloud image-based backup that can be used to restore data and applications even if your server is destroyed, and that can restore data from different points in time.
- Print a copy of your important/emergency contacts and take them with you if you do not have access to them from your phone or computer, you'll have them available to use via a landline.
- RealTime Clients: Everyone who is on our Business Continuity Service – Your servers are backed up and replicated offsite daily. If there is a problem, we correct that as part of the service. As hurricanes approach your physical location, we’ll be talking with you and confirm things are backed up and replicated prior to you shutting your operations down as part of your storm prep.
2. SECURE YOUR EQUIPMENT
- COMPUTERS
- Shutdown the operating system.
- If connected to a surge protector or UPS - unplug from the wall outlet (or unplug power cables from the surge protector or UPS if wall outlet isn't accessible).
- Unplug Ethernet cable from the back of computer or docking station.
- PRINTERS
- Power off the printer.
- If connected to a surge protector - unplug as described above.
- Unplug the Ethernet cable from the back of the printer.
- Unplug the phone cable from the back of the printer (if a fax line is connected).
- SERVERS AND NETWORK EQUIPMENT
- Perform a normal shutdown of the servers. RealTime clients: Please coordinate with RealTime service desk.
- Unplug all connections - Take photos to document how things were prior to the event.
- Firewalls, Switches, Access Points - unplug them from power. Unplug the firewall from the internet connection as well. Ideally, unplug all the network connections (surges can travel through the network cabling).
- Battery backups - power these off and then unplug them.
- Phone systems - Check with your vendor to see what steps you can take to protect it.
3. PROTECT FROM WATER/WIND
When a major storm is predicted, elevate your CPUs, printers, servers, and other network devices, as well as other electrical appliances like space heaters, off of the floor. For high winds, move computers away from windows. If there is a possibility of water leakage, cover computer equipment with plastic.
4. CONTINUING OPERATIONS AFTER THE STORM
- If you are in the path, power and internet connectivity may be hard to come by for a few days. Generators can provide enough power to run your critical computer equipment – just be sure you are connecting up to something that can deal w/ the power fluctuations many generators have. Please ask RealTime before connecting things up to generators as they can damage sensitive equipment. Modern battery backups may have the capability to condition the power off of a generator – check with the manufacturer to confirm before trying this.
- 4G USB modems or Mifi can get you connected in an emergency. Everything you do may not work, but basic web browsing.
- Forward your phones – If the office is expected to be out a few days, most phone service providers have a way for you to forward calls to your business to a cell phone or alternate number. Get the steps now, before you need them.
5. BE PREPARED
Knowing what steps to take ahead of time will help you be prepared in the worst-case scenario. RealTime is committed to ensuring our clients are prepared with the proper technology to meet their current/future needs as well as advising them about safeguarding their business from weather-related, cyber and other disasters.
If you would like further information about RealTime managing Information Technology for your business, contact us at info@realtime-it.com.
TECHNOLOGY SCAMS IN YOUR MAILBOX
You probably don’t remember signing up, but it’s just one of a hundred and ten things related to technology you probably don’t think about too often. This letter is designed to trick you into parting with some money, in this case, $228.00.
DID I FORGET TO PAY AN INVOICE?
To the unsuspecting, the above image looks like a legitimate invoice. You probably don’t remember signing up, but it’s just one of a hundred and ten things related to technology you probably don’t think about too often. This letter is designed to trick you into parting with some money, in this case, $228.00.
WHAT EXACTLY ARE THEY SELLING?
Just what they say, a website listing service. If you pay them, they will list your business on their own website. That’s it. This has no value for any business but theirs.
If you read this letter carefully, they do clearly state that you don’t have to do this, but most everything else is geared towards convincing you into sending them a check. We saw a rash of these misleading business practices a few years ago and just got wind of one today that we wanted to share as a reminder to be on your toes. I note that the wording has changed a bit since the last time I encountered this, probably due to lawsuits. It even says that this is a solicitation, something new for this year.
I logged onto the website and while a legitimate website and business (albeit worthless,) it is unfortunate that close to 10,000 businesses have fallen for this, which comes to close to 3 million dollars – I can see why this unsavory business is still around and still hunting suckers.
A WORD OF ADVICE
Our advice to our clients regarding any solicitations regarding their domain name, website, internet marketing, social media, computers, technology support, and the like, that you are not 100% sure is legitimate is to contact us before you commit to anything so that we can make sure someone isn’t trying to scam you.
*Some older versions even say that they are Accredited by the Better Business Bureau, but they aren’t.